A rare (if short-lived) victory, fake news and… a black cat?
“Sophisticated tactics and a ruthless approach.” In the world of cyber security that description would usually apply to the actions of a particularly adept ransomware group. In a refreshing change, however, in February the compliment went to the law enforcement agencies behind Operation Cronos. The UK’s National Crime Agency and the US FBI scored a rare and significant victory against the LockBit gang. The celebrations did not last long, as LockBit were back on a different site within days, but even so it has damaged the group’s reputation and will have sparked panic in the ranks.
The other February cyber headlines were dominated by the supply chain breach of Bank of America, and the ALPHV (aka BlackCat, aka Noberus) attack on Prudential Financial.
But which one of these stories is beginning to look like fake news?

1. Bank of America customers on alert: data potentially exposed in third-party breach
Summary
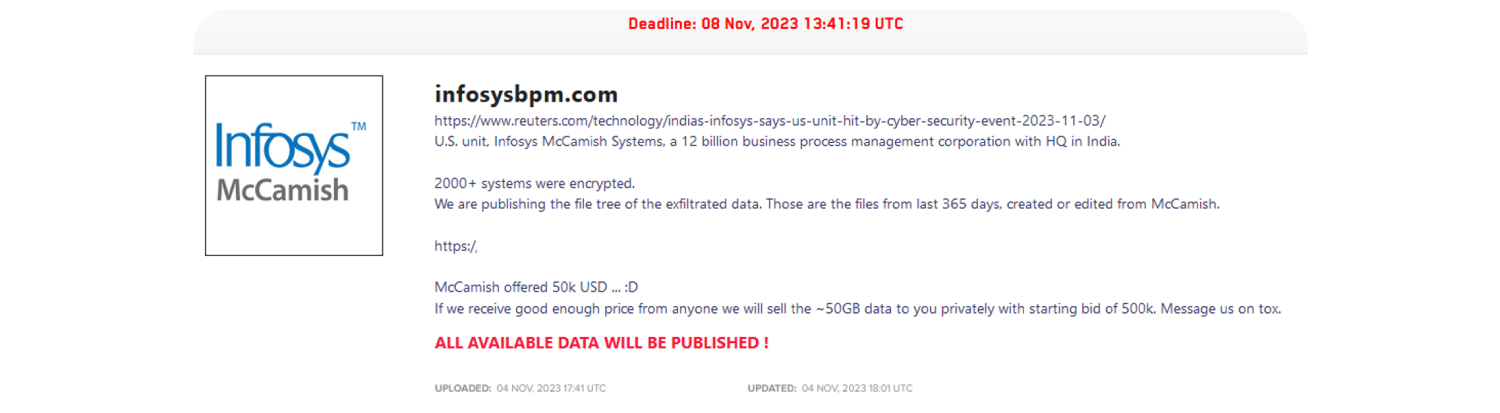
Thousands of Bank of America customers are on alert after a data breach at Infosys McCamish Systems (IMS). IMS is a third-party vendor handling deferred compensation plans on Bank of America's behalf. The incident highlights the growing risk of supply chain attacks on financial institutions through their third-party suppliers.
What happened
The LockBit group compromised IMS systems on 3 November 2023. The ransomware attack potentially exposed the personal information of 57,028 Bank of America customers with deferred compensation plans.
Exposed data may include names, addresses, dates of birth, social security numbers, and other account details.
Bank of America has notified affected customers, and offered two years of complimentary identity theft protection services.
What we know
Threat actors did not breach Bank of America directly. This is often the case with cyber attacks on financial institutions. Cyber criminals find it much easier to target those in the supply chain entrusted with sensitive customer data instead.
No confirmation exists of actual data misuse in this case. Even so, the risk of identity theft and financial fraud remains.
The bigger picture
This incident underscores the growing importance of robust cyber security measures for both financial institutions and their supply chains. It highlights the need for increased transparency and communication during data breaches to minimise customer anxiety and potential harm. Here’s a breakdown of the key cyber risks emanating from the supply chain:
- Third-party vulnerabilities: Your suppliers are like extensions of your own network. Any weak links in their cyber security can provide openings for attackers. Outdated software, inadequate access controls, and lack of employee training are common weaknesses found in third-party systems.
- Ransomware attacks: Targeting your suppliers with ransomware can indirectly disrupt your operations by halting their ability to deliver essential goods or services. You may even get caught in the crossfire if attackers gain access to shared data or systems.
- Malware infiltration: Malicious software introduced through your suppliers can infect your systems, leading to data breaches, financial losses, and operational disruptions. This can happen through infected software downloads, phishing attacks, or physical access to devices.
- Data breaches: Your sensitive information (such as customer and employee data, intellectual property, or financial records) can be shared with suppliers, and/or exposed through a data breach on their systems. This can lead to regulatory fines, legal issues, and reputational damage.
- Supply chain espionage: Cyber criminals may target your suppliers to steal valuable intellectual property, trade secrets, or confidential business information. This can undermine your competitive advantage and cause significant financial losses.
- Denial-of-service attacks: Attackers may target your suppliers to launch distributed denial-of-service (DDoS) attacks that disrupt their internet connectivity and ability to serve you, essentially blocking access to critical resources or products.
- Man-in-the-middle attacks: Hackers can intercept communications between you and your suppliers. They can then manipulate data or inject malware, leading to compromised systems and unauthorised transactions.
- Counterfeit software/hardware: Malicious actors may introduce counterfeit software or hardware into your supply chain. This can contain hidden malware or backdoors that grant unauthorised access to your systems.
2. Prudential affected by ALPHV
The cyber security landscape is a battlefield, and financial institutions are prime targets. The ALPHV ransomware group, also known as BlackCat, recently claimed responsibility for attacks on LoanDepot and Prudential Financial. But with conflicting reports and limited information, the true picture remains murky.
Prudential acknowledges incident, denies data breach
In February 2024, news outlets reported that ALPHV listed both LoanDepot and Prudential as its victims.
Prudential confirmed an unauthorised access attempt in an official filing. The data breach compromised employee and contractor data, but did not involve any customer or client data. The type of attack and methods used remain unconfirmed, however ALPHV do mention that they possess legitimate credentials.
ALPHV makes bold claims, but are they true?
ALPHV (also known as BlackCat and Noberus) is a prominent Ransomware-as-a-Service (RaaS) group. It has been a significant threat in the cyber security landscape ever since it emerged in late 2021. It has targeted various industries (including finance, healthcare, and government entities) with sophisticated tactics and a ruthless approach.
Key characteristics
- RaaS model: ALPHV operates through a RaaS model. It provides malware and support to affiliates who share a portion of the ransom payments.
- Technical sophistication: ALPHV utilises the Rust programming language for encryption, making data recovery challenging. They also employ double extortion tactics, encrypting data and exfiltrating it for potential public release, increasing pressure on victims.
- Targeted attacks: ALPHV exhibits specific industry targeting, focusing on high-impact sectors with potentially devastating consequences.
ALPHV's data leak website lists both companies, suggesting a successful breach. It even claimed continued access to Prudential's network and threatened to release stolen data. Prudential, however, says it is still investigating the extent of the incident.
There has been a recent trend of ransomware gangs falsely claiming to have access to data, because they know the implications for their victims – particularly those victims in regulated industries. These false claims show an increasing desperation as more organisations are refusing to pay ransoms.
At the time of writing, it is impossible to determine which data hackers have exfiltrated. If ALPHV is indeed telling the truth, it is likely that the group will share its proof on its shaming site. But it is reasonable to expect that ALPHV would have done this by now, and the data may never materialise.
3. LockBit shaming site seized

The NCA and international law enforcement dismantles notorious LockBit ransomware group (for a while, at least)
A coalition of international law enforcement agencies successfully disrupted the operations of the LockBit ransomware group in February 2024. This takedown, which involved the UK’s National Crime Agency (NCA) and the FBI, is significant for several reasons.
LockBit's impact
- In the last two years, LockBit was responsible for at least 1,700 attacks and was by far the most prolific and destructive ransomware group. It extorted victims across the globe, including hospitals, schools, and critical infrastructure providers.
- Its attacks resulted in severe financial losses and operational disruptions for countless organisations, including a recent devastating attack on a children’s hospital.
Takedown details
- The operation involved seizing critical infrastructure, like servers, and disrupting the group’s online communication platforms.
- Authorities also arrested two key members of the group, who are accused of involvement in numerous ransomware attacks.
- Notably, this takedown demonstrates international cooperation and coordination in combating cyber crime.
The takedown doesn't eradicate the entire ransomware ecosystem. Disrupting a prolific group like LockBit does, however, send a strong message. It also eased the immediate pressure on targeted sectors.
To add insult to LockBit’s injury, the NCA and FBI used its shaming site to post about their own activities and offer guidance to LockBit's victims. They then took the site offline on 24 February.
This feeling of triumph did not last long. As expected, LockBit returned with a new shaming site and a new list of victims. It also addressed the takedown and how it believes law enforcement was able to do it. The group added an element of conspiracy by stating that it was targeted because it has information on Donald Trump that could affect the upcoming US election. LockBit has since stated that it will target “.gov” domains more often.


Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Thomas Murray launches Cyber Risk practice with key strategic hire
Leading global risk intelligence firm Thomas Murray has announced the launch of its Cyber Risk advisory practice today with the key strategic…

Tabletop exercises: Where to start
Knowing how to deal with the fallout from a major cyber incident is just as important as knowing how to prepare for one. In cyber security…

Thomas Murray announces Malta agreement with Diligex
Thomas Murray, the global risk intelligence and cyber security firm, today announced a distribution agreement with Diligex. Diligex is a…